The holiday season is in full swing, and cybercriminals are working full time to devise the best schemes to fill their stockings with your banking details. It is no longer enough to stay alert for misspellings, typographical errors, fake logos, and odd or hilarious narratives in your inbox. Today’s attacks are usually more sophisticated than the oft-cited Nigerian prince or the vacationing nephew held at the consulate after his wallet and passport were stolen. Brett Creasy, President and Director of Digital Forensics for bit-x-bit points out that “It is important for everyone to keep in mind what the tactics of the bad actors are, and the fact is 32% of breaches in the past year involved phishing.[1] Even if the numbers in some segments are going the right way, it still makes up a huge portion of attacks.”
How do attackers package their phishing attacks? Some phishing attempts arrive in the body or attachments of an email, while others are transmitted via text message. Social media sites such as Facebook and LinkedIn offer another avenue for phishing lures, and attackers frequently take the time to get to know a potential victim’s friend list and other available facts about their career and life history. Attackers are savvy and will do their research to determine the best recipients for their message—an employee with administrative access to a company’s server, for example.
Attackers may provide minimal detail and ask you for something that seems entirely ordinary. They may be familiar with your industry (such as legal, supply chain, medical, or technical), the applications you are likely to use in your work, or the style of reports you might expect to receive as an attachment. The message may seem to come from a friend, family member, or colleague, spoof a domain name, or look just like a trustworthy company or organization. This kind of attack is known as “spearphishing” and is growing more popular among attackers.
The best defenses against phishing attacks are patience and reflection before taking any action. Question any request that seems out of place or highly urgent. Timing should be a core consideration: if you’ve already been charged for a monthly streaming service, it’s unlikely that your account credentials have expired, and there’s no need to act. Avoid falling victim to false urgency at work by heading straight to the source. If you receive an unexpected email from your boss asking you to transmit confidential information or security credentials, pick up the phone or drop by in person. After verifying, provide any sensitive information over a secure channel, and document your efforts. It is important to report any phishing attempts to IT/information security.
During the holiday season (as well as tax season), phishing scams like the ones described above can arrive in droves. Don’t let it wreck your holiday spirit—instead, stay alert. Requests for passwords, account numbers, financial details, security details, or any personal, health, or financial information should automatically raise suspicion. In these cases, avoid opening any attachments or clicking on links within the body of an email or message. Instead, in a separate window, open your web browser and visit the company’s website to login, or call the organization’s support line to verify the request.
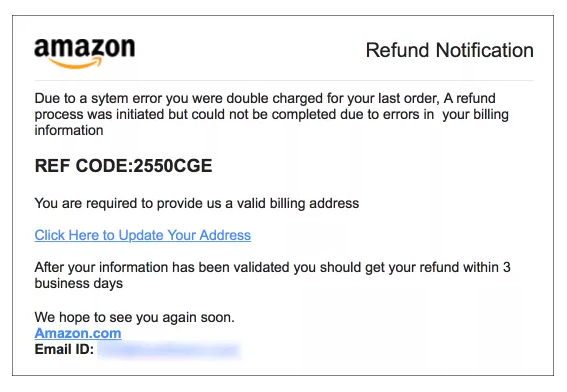
Below is an example of a scam Amazon email that asks the recipient to click a link to update their billing address. In addition to looking for misspellings (such as “sytem” instead of “system”), one way to recognize a scam like this one in your own inbox is to hover over the links in the message without clicking and wait to see whether the URL actually points to the correct website.
If you believe you have fallen victim to a phishing scam, call us at 412-325-4033 or visit www.bit-x-bit.com to learn more about bit-x-bit and discover how our integrated risk and response services can protect your company from electronic data theft and security issues—now and in the future.
[1] The 2019 Data Breach Investigations Report by Verizon.